If you encounter a ABSTAIN vote from the Policy/Security Framework of Flow, you might have misspelled something – read here to learn how to validate your configuration
Debugging a ABSTAIN vote in the Policy/Security framework of Flow Framework
This is learning by doing/debugging – a gift from me to you, after three days of scratching my head.
The issue at hand
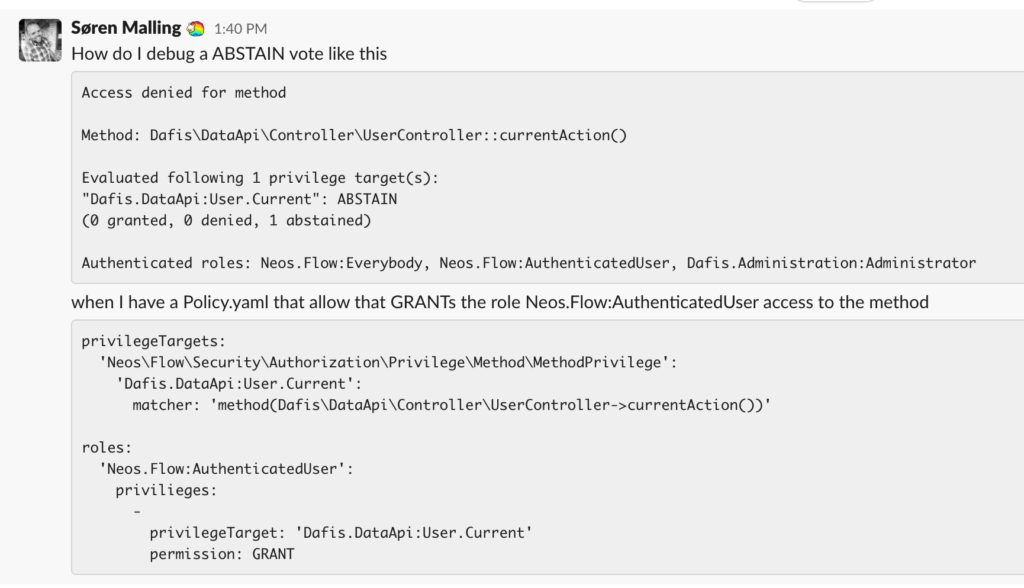
I had authenticated and then requested a route, that my authentiated Account was granted permission to. My Policy.yaml looked like this
privilegeTargets:
'Neos\Flow\Security\Authorization\Privilege\Method\MethodPrivilege':
'Dafis.DataApi:User.Current':
matcher: 'method(Dafis\DataApi\Controller\UserController->currentAction())'
roles:
'Dafis.DataApi:ApiUser':
privilieges:
-
privilegeTarget: 'Dafis.DataApi:User.Current'
permission: GRANT
But, Flows policy enforcer (the security-checking-mechanism) keept throwing this “you are not allowed”-exception at me
Access denied for methodMethod: Dafis\DataApi\Controller\UserController::currentAction()Evaluated following 1 privilege target(s): "Dafis.DataApi:User.Current": ABSTAIN (0 granted, 0 denied, 1 abstained) Authenticated roles: Neos.Flow:Everybody, Neos.Flow:AuthenticatedUser, Dafis.DataApi:ApiUser
Flow kept telling me that none of my roles for my authenticated account (see the list of roles at the end of the exception) was allowed. But my Policy.yaml told me otherwise (at least I thought)
The solution (hint: it’s a typo)
I’ve spend 3 days back and forth, shorter and longer time spans, debugging, trying to solve this. Spending 3 hours on this sunny day debugging my way into privileges and how that works. And then I wrote on the Neos project Slack for help
First I share the issue
I add some more details, outputs from the CLI commands available
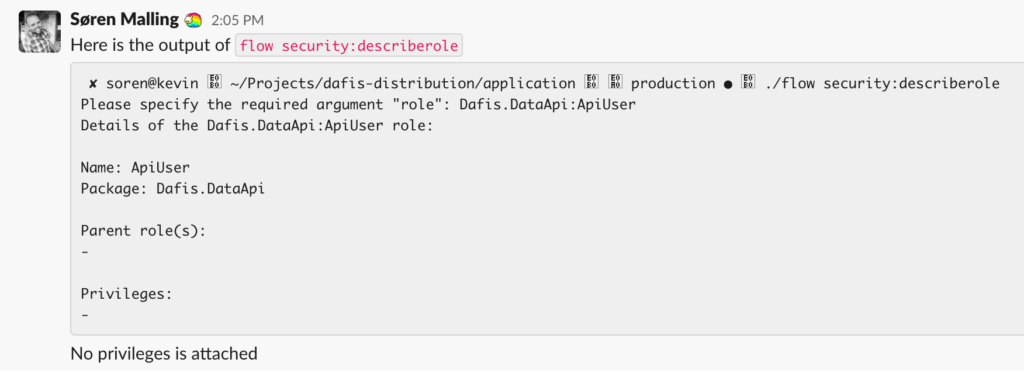
security:describerole commandAnd then I see it..
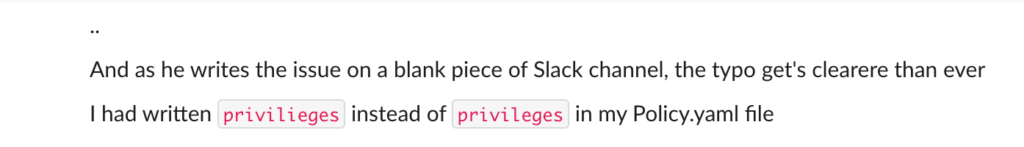
So, I’ve mistyped privileges and instead wrote privilieges. A clear mistake. Change it, and the security framework does as I hoped for.
What could I have done – Configuration Schema Validation!!!
We are here to learn everyday – and especially me!
One thing that I have wondered about, was the many *.schema.yaml files found in the Neos.Flow. And today I found out why they are usefull!
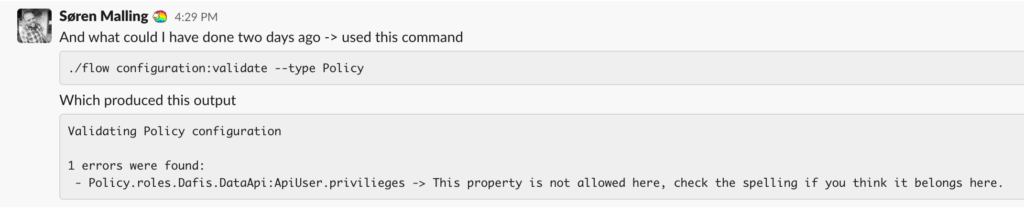
Since there is a schema file for the Policy.yaml configuration format I could use the CLI command
./flow configuration:validate --type Policy
which gave me (with the wrongly types privilieges)
Validating Policy configuration
1 errors were found:
- Policy.roles.Dafis.DataApi:ApiUser.privilieges -> This property is not allowed here, check the spelling if you think it belongs here.And I could conclude the same in the Slack channel with this message: